There is an old adage that if you can’t measure something, then you can’t manage it. This holds particular truth to a security team. So many of today’s security teams are working with ad-hoc processes, and lack of structure. Many companies don’t even have security teams, but instead rely on their IT or Engineering teams to compensate. This isn’t necessarily bad, but how do you know that your risk appetite is truly being handled appropriately?
Maturity assessments are that tool. Mapped to a known framework, you can reliably judge your security program, and apply efforts towards domains that are measurably lacking. The most well known maturity model is probably the DoD’s Cybersecurity Maturity Model Certification (CMMC).
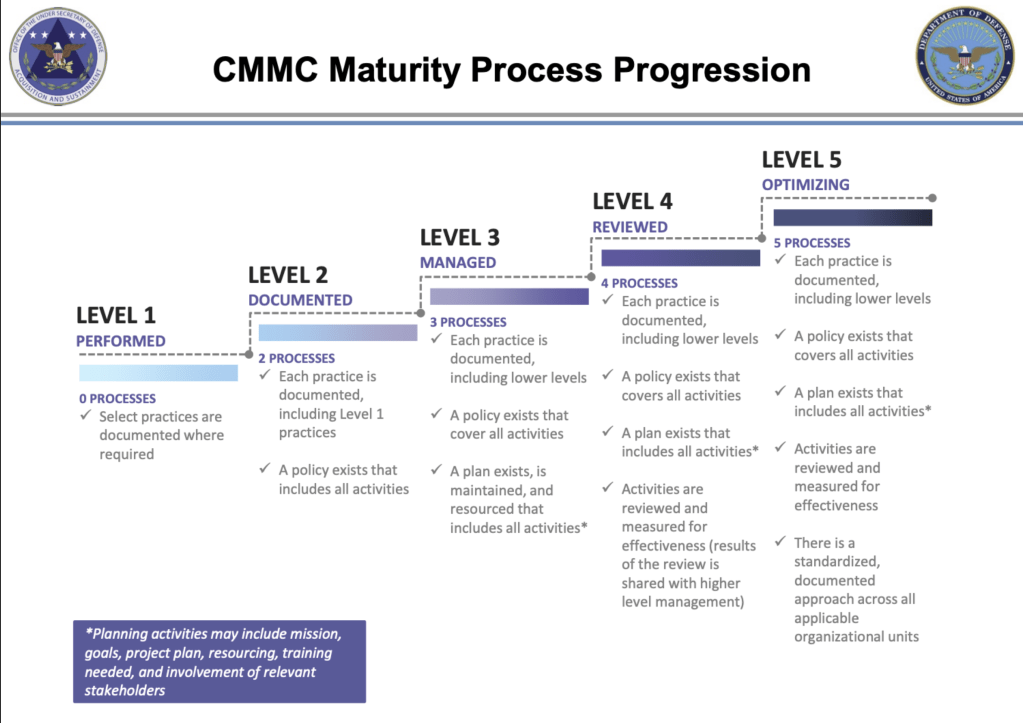
This model provides teams with a view on how well prepared they are for a security event. If done regularly, if can provide teams with the satisfaction of showing visible growth across the different domains. Those domains are outlined here:
CMMC Assessment Domains:
- Access Controls (AC) – Limiting user access to information systems
- Asset Management (AM) – Documentation of known equipment and approved assets
- Audit & Accountability (AU) – Ability to track user actions to the individual
- Awareness and Training (AT) – Measures taken to educate your workforce
- Configuration Management (CM) – Appropriate configuration, limitation, and use of documented systems
- ID & Authentication – (IA) – Identifying end users correctly and their ability to access systems (multifactor authentication at CMMC Level III)
- Incident Response (IR) – Cybersecurity breach and organizational disaster recovery and business continuity planning
- Maintenance (MA) – Performance of regular maintenance and software updates
- Media Protection (MA) – Proper disposal, transfer, and housing of FCI and CUI data
- Personnel Security (PS) – Screening and authorizing users before accessing data, prevention of data loss through employees
- Physical Protection (PE) – Limiting physical access to resources and monitoring building activity
- Recovery (RE) – Data backup and recovery strategies, maintaining data integrity
- Risk Management (RM) – Identifying and mitigating environmental vulnerabilities
- Security Assessment (CA) – Develop, document, and continually improving security postures
- Situation Awareness (SA) – Metric of adapting to latest security exploits and threat mitigation
- Systems and Communications Protections (SC) – Defining and controlling environment security boundaries, and monitoring for appropriate usage
- System and Information Integrity (SI) – System updates, identifying malicious content, employing monitoring systems to maintain integrity, protecting e-mail communications
How does an assessment work?
We here Druid Security believe that adopting frameworks like the CMMC, NIST Cybersecurity Framework, or ISO 27001 can help teams develop their capabilities into fully mature programs. During an assessment we work closely with your Security, IT, and other teams in order to conduct in depth interviews and collect detailed evidence. These interviews are confidential, and done with the idea of assisting the organization to level up their capability.
Once the evidence collection is complete, you will receive a comprehensive assessment package, including white papers, recommendations, and tooling guides. Like a good post mortem, the goal of this exercise is to not only recognize gaps and problem areas, but also highlight mature people, processes, and technology that you have already invested in.
To close, if you are looking to start measuring your programs, give us a call. We are here to help!